
Is This the Year Everyone Realizes What a Great Cloud Solution OneDrive is?
If you’re looking for an easy way to share your files to the cloud then OneDrive is the answer. It may have taken awhile for
A collection of articles that will keep your South Carolina business secure, productive, and profitable. Our blog covers a wide range of topics, from cybersecurity to productivity tips, designed to help you navigate today's digital landscape with confidence.
We share strategies for optimizing your IT support, protecting your valuable data, and leveraging Microsoft 365 security features effectively. Stay informed about the latest trends and best practices in cybersecurity, budgeting, and running a business.

If you’re looking for an easy way to share your files to the cloud then OneDrive is the answer. It may have taken awhile for
$12 billion per year, that’s how much revenue is reportedly lost in the Healthcare industry due to poor communication, according to Dr. James Woodson, MD,

Employee Retention is at An All-Time Low According to Work Institutes 2018 Employee Retention report, employers paid a whopping $600 billion in turnover costs

Remote Devices Provide a Weak Link for Hackers to Exploit The internet of things (IoT) and office policies of “bring your own device” BYOD, have

Ten years ago, it wasn’t that hard to protect your online accounts – a simple password would do just fine for the most part (along
If you’re a Windows 7 user, you may have already heard that mainstream support for Windows 7 has ended and security updates will stop in
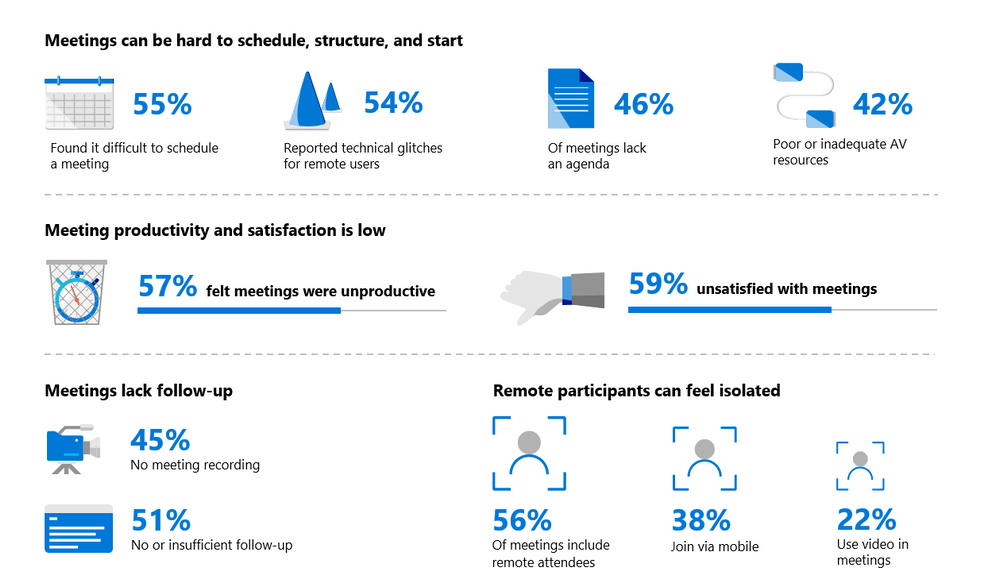
One thing modern businesses can count on is having meetings. As more teams work remotely and different partners colloborate all over the world, the number
At PTG, we enjoy being able to solve user problems with Office 365. It’s this commitment to the user experience that has helped make us
Working smarter – not harder is a goal for many people this year. As screen time and the number of meetings increases for just about
This is Part 2 in a Blog Series About Email Subscription Bombs, Read Part 1 Here. Email Security Best Practices While every type of attack