How Can Data Security Be Implemented?
Data Security Methods That Are Effective for SMBs to Protect Themselves Against Today’s Risks.
A collection of articles that will keep your South Carolina business secure, productive, and profitable. Our blog covers a wide range of topics, from cybersecurity to productivity tips, designed to help you navigate today's digital landscape with confidence.
We share strategies for optimizing your IT support, protecting your valuable data, and leveraging Microsoft 365 security features effectively. Stay informed about the latest trends and best practices in cybersecurity, budgeting, and running a business.
Data Security Methods That Are Effective for SMBs to Protect Themselves Against Today’s Risks.
A majority of online users have had some of their personal identity data exposed in one of the thousands of major breaches that’s occurred in
There is no such thing as completely bulletproof security. Every software has vulnerabilities. However, there is one security tool that has been found to block
Email management in 2019 can be overwhelming. It helps to have some tips to improve the quality of the messages you send, plus enhance focus
Baltimore — as in the entire city, has been dealing with the ramifications of a cyberattack that froze thousands of computers, brought emails to a
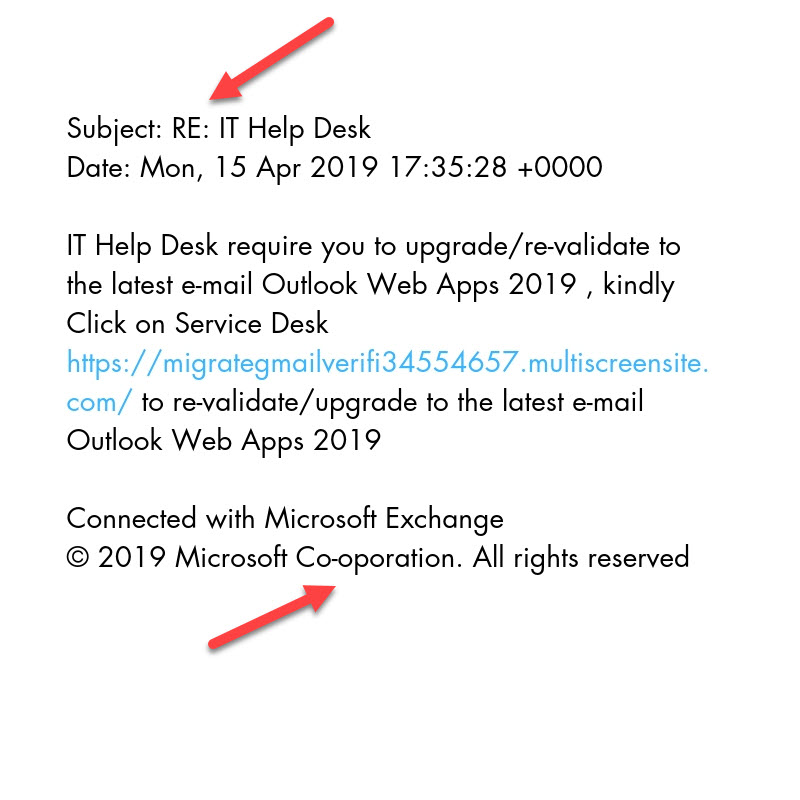
We always see an increase in phishing attacks right before tax season and into travel-heavy summer. This year is no different.

Every day our cybersecurity team investigates and fights against a wide variety of phishing emails and spoofing attacks.
This is Part 2 in a Blog Series About Email Subscription Bombs, Read Part 1 Here. Email Security Best Practices While every type of attack