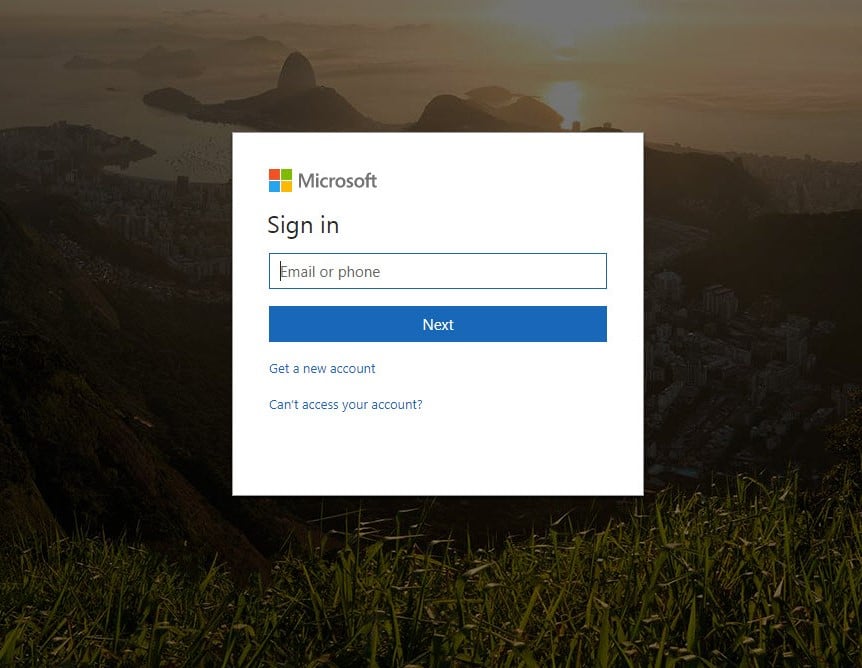
New Phishing Attacks Mimic Branded Microsoft 365 Login Pages
Phishing attacks are still on the rise. And hackers are getting more sophisticated in the ways they spoof elements in a user’s environment in order
A collection of articles that will keep your South Carolina business secure, productive, and profitable. Our blog covers a wide range of topics, from cybersecurity to productivity tips, designed to help you navigate today's digital landscape with confidence.
We share strategies for optimizing your IT support, protecting your valuable data, and leveraging Microsoft 365 security features effectively. Stay informed about the latest trends and best practices in cybersecurity, budgeting, and running a business.

Phishing attacks are still on the rise. And hackers are getting more sophisticated in the ways they spoof elements in a user’s environment in order

DEF CON is the world’s largest underground hacking conference. It’s been running since 1992 and is always a wealth of information about cybersecurity vulnerabilities.

Every day our cybersecurity team investigates and fights against a wide variety of phishing emails and spoofing attacks.

Okay, quick disclaimer, no crime was committed here. This person agreed to demonstrate how hackers operate as part of a service to keep business owners
This is Part 2 in a Blog Series About Email Subscription Bombs, Read Part 1 Here. Email Security Best Practices While every type of attack