
Fortifying Your Business: Essential Cyber Security Tips
Cybersecurity management is critical as each device on your network can be a potential entry point for threats. Learn essential tips to enhance your business’s
A collection of articles that will keep your South Carolina business secure, productive, and profitable. Our blog covers a wide range of topics, from cybersecurity to productivity tips, designed to help you navigate today's digital landscape with confidence.
We share strategies for optimizing your IT support, protecting your valuable data, and leveraging Microsoft 365 security features effectively. Stay informed about the latest trends and best practices in cybersecurity, budgeting, and running a business.

Cybersecurity management is critical as each device on your network can be a potential entry point for threats. Learn essential tips to enhance your business’s

Hopefully, you’ve never run into this problem, but if you have and you’re looking for answers… Welcome. Refreshments are on the left. One day
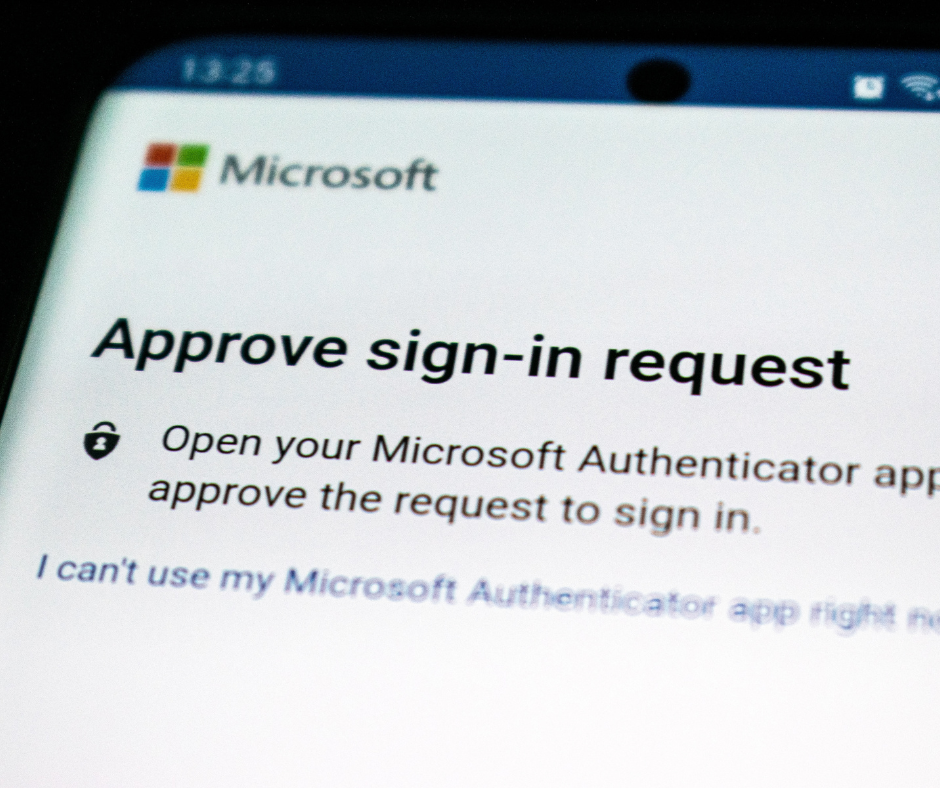
Back in October 2019 – you know, before it all changed – Microsoft beta-tested a new baseline security program with 30 million users. We let the mega-computers
If you’re reading this, you’re probably pretty proactive when it comes to cyber security. You’re also probably well aware of the benefits of keeping terabytes
No matter the industry you’re in if you’re collecting information, you should be protecting that data. And to protect that data, you’ve undoubtedly run
Data Security Methods That Are Effective for SMBs to Protect Themselves Against Today’s Risks.
A majority of online users have had some of their personal identity data exposed in one of the thousands of major breaches that’s occurred in
There is no such thing as completely bulletproof security. Every software has vulnerabilities. However, there is one security tool that has been found to block
Compliance and privacy can no longer be put on the back burner by businesses. Companies today face serious risks if they fail to stay compliant.
This is Part 2 in a Blog Series About Email Subscription Bombs, Read Part 1 Here. Email Security Best Practices While every type of attack