Thinking critically, and a little bit for fun, we were trying to come up with other ways “Endpoint” and EDR could be misinterpreted or misunderstood. Maybe the end of a maze, or a weird way to think about the idea of a finish line? An offshoot of the revolutionary dancing video game Dance Dance Revolution (DDR), even.
But at the end of the day, Endpoint Detection and Response – and all that goes along with it – is a straightforward topic we can clarify shortly. You don’t need to memorize dance moves or contemplate deep meanings to understand this one.
No, we are here today to answer three of the most frequent questions we get:
- What are endpoints
- Why do endpoints need protection
- How does this EDR thing help protect my endpoints?
{{cta(‘4de33c46-6119-4467-a300-503043c72df0′,’justifycenter’)}}
What are endpoints?
In the IT context, an endpoint is any remote device that communicates back and forth with a network to which it is connected. That means any sort of Internet of Things (IoT) devices like:
- Desktop computers
- Laptops
- Smartphones and tablets
- Servers
- Remote workstations
These devices represent perfect places for cybercriminals to enter your network. These endpoints are exactly where attackers want to exploit using special code aimed at your most precious data.
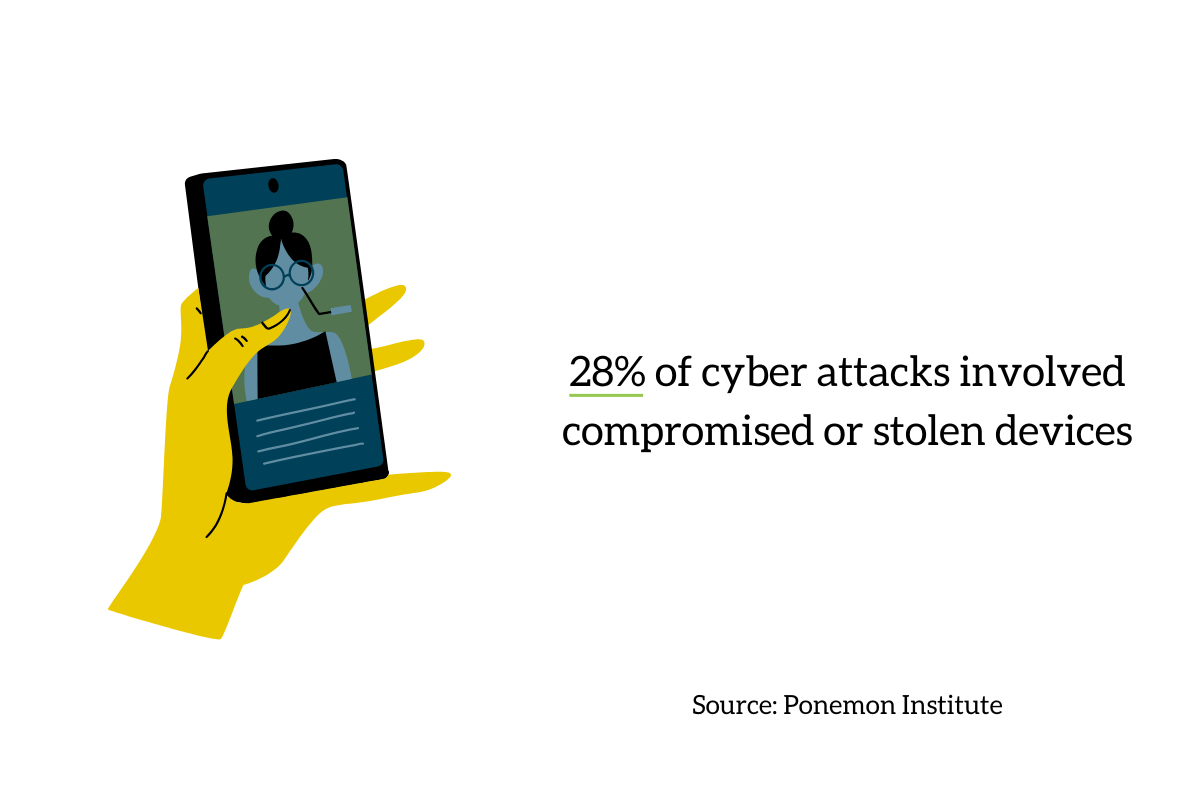
Attacks don’t just come from one place either. While the Ponemon Institute found 81% of businesses experienced an attack involving some form of malware, and 28% experienced attacks involving compromised or stolen devices.
And now, as the workforce is as remote as ever – and likely pushing further in that direction in the future – there are considerably more opportunities for cyber criminals to find ways into your network.
Why do endpoints need protection?
Endpoint attacks are incredibly common in today’s hybrid workplace. Additional research from the Ponemon Institute found 68% of organizations have experienced one or more endpoint attacks that successfully compromised data and/or their IT infrastructure.
As if acting as portals into your network wasn’t bad enough, the reality of the situation is endpoints are one of, if not the, most important places to protect your business, regardless of size and industry. The Verizon DBIR has revealed that the human element is responsible for 82% of all successful breaches. Without proper education and training, most folks just don’t know what to look out for. In 2022, IBM and the Ponemon Institute estimated the average cost of a data breach is $4.35 million.
Which employees need cyber security training? Why You Need to Implement Cyber Security Training Today
And if your people aren’t protecting their devices correctly, things can get worse. According to Uptime’s 2022 Data Center Resiliency Survey, nearly 40% of organizations have suffered a major outage caused by human error over the past three years, and over 60% of these kinds of outages result in at least $100,000 in total losses.
Bad actors are getting better and better at getting into devices, too. Aside from just stealing and decoding devices, nefarious folks are now “juice jacking” which is a totally real phrase where they are modifying USB ports to automatically install malware onto the victim’s device. These ports are disguised as free chargers aimed at remote workers. One report found 79% of people traveling for business have connected their devices to a public USB port or charging station – unknowingly opening the door for a potential attacker.
If you are interested in how EDR can work in your organization,
click here!
Of course, attackers are looking mostly to use your endpoints as an entry and exit point for high-value assets, but they are also able to hold hostage your endpoint devices if they are able to gain access. They can even use your devices in the commission of another crime, which can put your team in a whole new realm of hurt.
The best news about all of this? There exists a system called Endpoint Detection and Response that can keep your team safe and vigilant.
What is EDR & how does it help protect endpoints?
So, endpoints are devices, and they need protection because otherwise people can steal your data, which will cost you in all kinds of ways.
That just leaves Endpoint Detection and Response to talk about.
Sometimes with the word “Threat” in there, too, EDR is a security solution that monitors your endpoints (devices, stuff, however you want to say it) to be constantly vigilant in the fight against intrusions like ransomware and malware. Think of it as zero-trust architecture put into constant practice digitally.
Gartner’s Anton Chuvakin says EDR is defined as a solution that “records and stores endpoint-system-level behaviors, uses various data analytics techniques to detect suspicious system behavior, provides contextual information, blocks malicious activity, and provides remediation suggestions to restore affected systems.”
“[EDR] records and stores endpoint-system-level behaviors, uses various data analytics techniques to detect suspicious system behavior, provides contextual information, blocks malicious activity, and provides remediation suggestions to restore affected systems.”
You may be wondering how it works. Wonderful.
Primarily, EDR systems monitor and collect activity data from each device and review each action to determine if a threat is present, while actively learning from each encounter and monitoring for future threats differently. Additionally, the system will automatically respond to threats it finds, removing them while notifying your IT team of the intrusion. When a threat is found, the system will also use forensic tools to dig into your system to be sure nothing suspicious has taken place.
*DEEP BREATH*
Conclusion
Here’s the straightforward truth: EDR is great for businesses in the modern era and you should consider using it. According to Stratistics MRC’s Endpoint Detection and Response – Global Market Outlook (2017-2026), the adoption of EDR solutions is expected to reach an annual growth rate of nearly 26%, meaning businesses are seeing the value EDR brings. Whether your team has gone remote, works hybrid, or just has a lot of endpoints, there are plenty of opportunities for EDR to work for your organization.
If you have further questions about the ways your business can strengthen its security through EDR solutions, give us a call at (864) 552-1291 and we’ll help you evaluate capabilities and options. Also, sign up for PTG Tech Talk for bi-monthly tech news, and consider following us on LinkedIn, Facebook, and Twitter!